HIJACKING A FACEBOOK ACCOUNT WITH SMS.
This post will demonstrate a simple bug which will lead to a full takeover of any Facebook account, with no user interaction. Enjoy.
Facebook gives you the option of linking your mobile number with your account. This allows you to receive updates via SMS, and also means you can login using the number rather than your email address.
The flaw lies in the
/ajax/settings/mobile/confirm_phone.php end-point. This takes various parameters, but the two main are code, which is the verification code received via your mobile, andprofile_id, which is the account to link the number to.
The thing is,
profile_id is set to your account (obviously), but changing it to your target’s doesn’t trigger an error.
To exploit this bug, we first send the letter F to 32665, which is Facebook’s SMS shortcode in the UK. We receive an 8 character verification code back.
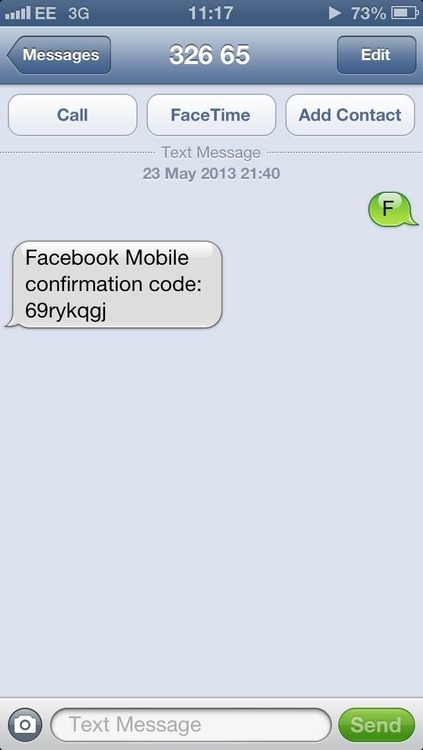
We enter this code into the activation box (located here), and modify the
profile_id element inside thefbMobileConfirmationForm form.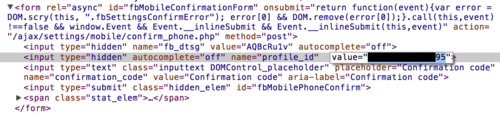
Submitting the request returns a 200. You can see the value of
__user (which is sent with all AJAX requests) is different from the profile_id we modified.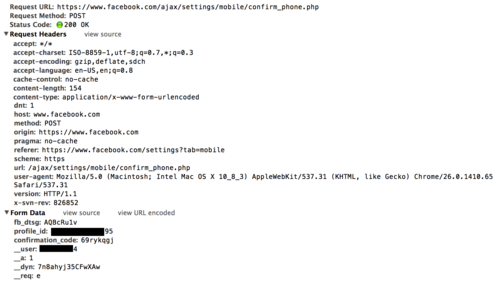
Note: You may have to reauth after submitting the request, but the password required is yours, not the targets.
An SMS is then received with confirmation.
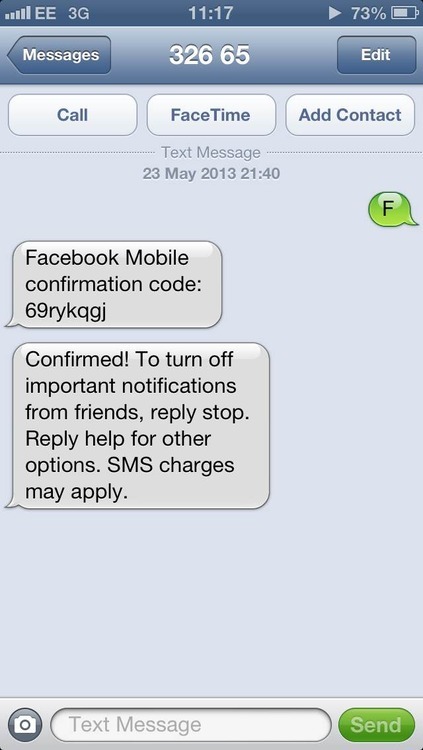
Now we can initate a password reset request against the user and get the code via SMS.
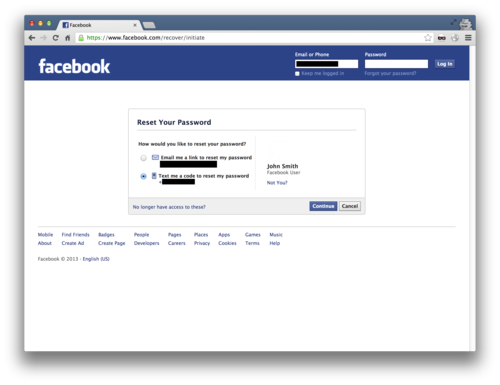
Another SMS is received with the reset code.
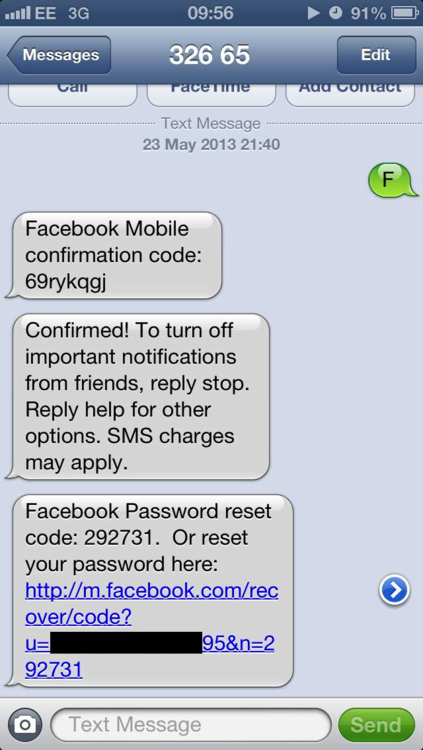
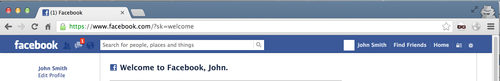
We enter this code into the form, choose a new password, and we’re done. The account is ours.
Fix
Facebook responded by no longer accepting the
profile_id parameter from the user.Timeline
23rd May 2013 - Reported
28th May 2013 - Acknowledgment of Report
28th May 2013 - Issue Fixed
28th May 2013 - Acknowledgment of Report
28th May 2013 - Issue Fixed
Note
The bounty assigned to this bug was $20,000, clearly demonstrating the severity of the issue.
